Pass4itsure implementing latest Cisco DCII 300-165 dumps exam questions with the knowledge and skills for CCNP video series, Pass DCII Implementing Cisco Data Center Infrastructure (DCII). Pass4itsure offers a wide range of certification https://www.pass4itsure.com/300-165.html dumps exams for their different certifications based on their products and services.
Exam Code: 300-165
Exam Name: DCII Implementing Cisco Data Center Infrastructure (DCII)
Updated: Aug 25, 2017
Q&As: 165
[New Cisco 300-165 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWeTBEWVNsUmFmOEU
[New Microsoft 70-767 Dumps Version From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWaWpOOFpVd3ZyMTg
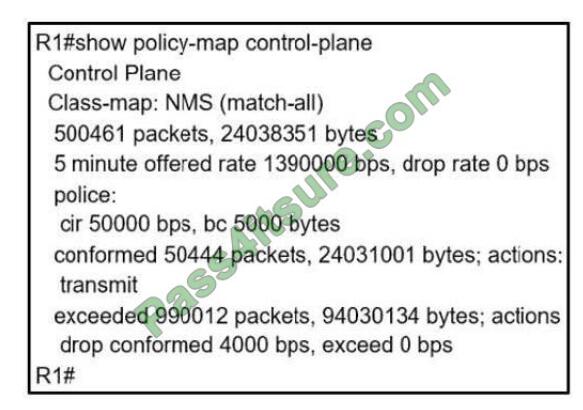
1.If a Replica instance is taken out of service by shutting it down but it is NOT removed from the
Operations Console instance list,
A.the Primary server will continue periodic attempts to communicate with the Replica.
B.the Primary server will assume the Replica is dead and will automatically change the status to inactive.
C.it could potentially be used to attack a network by adding a user and token to the Replica that would not
be validated by the Primary.
D.it cannot be restored to service without performing a Replica Installation Update procedure with a new
Replica Package from the Primary.
300-165 exam Answer:A
2.When an RSA Authentication Agent for Internet Information Services is first installed, access to web
site files and directories
A.is allowed by default until the web server host computer is re-booted.
B.is not changed until the ISM snap-in service is started using the system control panel.
C.is allowed by default but can be configured to require authentication to access certain objects.
D.initially requires authentication but can be configured to allow unauthenticated access to certain
objects.
Answer:C
3.Which of the following devices features the ability to restore its initial state from the host boot menu?
A.RSA Web Tier server
B.RSA Authentication Agent host
C.RSA SecurID hardware appliance
D.RSA Authentication Manager virtual appliance
300-165 dumps Answer:C
4.Which of the following tasks are associated with a Web Tier deployment for Risk-Based
Authentication?
A.integration script creation
B.user mobile phone registration
C.enable Windows password integration
D.verify there is no web Agent installation
Answer:A
5.When preparing for setup of RSA Authentication Manager, it is important to ensure
A.an accurate time source for the system.
B.that DHCP is enabled to assign a valid IP address to the host.
C.the correct sdconf.rec file is moved from an Agent to the server host.
D.that Agents and the host equipment are on the same network subnet.
300-165 pdf Answer:A
6.Which of the following BEST describes the Blend Shape deformer?
The Blend Shape deformer…
A. creates a joint system based on the topology of the surface
B. Blend shape deformers let you change the shape of one object into the shapes of other objects.
C. is a special object you use to control the deformation effects of rigid skinning.
D. lets you manually sculpt NURBS, polygons, or Subdivision surfaces quickly with the stroke of a brush
Answer: B
7.What is the syntax to add a single-line comment in a script.?
A. //
B. <>
C. ” D.
==
300-165 vce Answer: A
8.The ViewCube is an on-screen 3D navigation element that does which of the following?
A. Creates a multicamera rig to navigate through your scene
B. Provides feedback about stereo cameras and performs calculations to produce anaglyph images
C. Enables you to quickly and easily switch between views.
D. Provides feedback about the current camera view in relation to the 3D scene
E. Both C and D
Answer: E
9.Which of the following is a way to control deformations using a Smooth Bind?
A. Add Influence
B. Flexors.
C. Projection Box.
D. Both A and B
300-165 exam Answer: B
10.To composite two layers together you would use…
A. Composition settings
B. Garbage Mask
C. Remap Color
D. Blend & Comp
Answer: A
11.You have just attempted to perform DNS poisoning on the local network DNS server and
did not succeed;you decide to launch an attack against routing tables instead.
Which of the following would NOT be an effective way of attempting to manipulate the
routing table on the local network or through its gateway?
A.By using a source route attack
B.By using ICMP redirect messages
C.By adverstising bogus OSDF routes
D.By advertising bogus RIP routes
300-165 dumps Answer: C
12.Why is it so challenging to block packets from Remote Access Troans that use port 80
for network communications?Choose three.
A.To a firewall,the traffic appears simply to be from an internal user making an innoccous HTTP GET
request.
B.Port 80 outbound is normally open on corporate firewalls
C.Stateful inspection firewalls will block unsolicited inbound HTTP GET requests
D.Not all firewalls are capable of inspecing data in the HTTP data fields for evidence of tunneling
Answer: A,B,D
13.Which of the following statements would best describe the act of signing a message with
a Digital Signature?
A.The sender creates a hash value of the message he wishes to send He uses his private key to encrypt
the hash value.The message and the encrypted hash value are sent to the receiver.
B.The sender creates a hash value of the message he wishes to send.He uses his public key to encrypt
the hash value.The message and the encrypted has value are sent to the receiver.
C.The sender creates a hash value of the message he wihes to send.The message and the hash value
are sent to the receiver.
D.The sender uses his public key to create a digital signature.
The digital signature is sent along with the text message.The receiver will use the sender private key to
validate the signature.
300-165 pdf Answer: A
14.One of the last steps taken by an attacker will be to configure permanent access to a compromised
system.However, the installation of a backdoor, installation of new processes,and changes to key files
could be very quickly detected by an administrator.What tool would assist the attacker in preventing the
administrator from detecting changes to files,new processes that are running,or other signs that the
system might have been compromised?
A.A Trojan horse
B.A Rootkit
C.A Backdoor
D.A privilege escalation tool
Answer: B
15.Which of the following tools can detect hidden Alternative Data Streams on an NTFS file or
folder?Choose all that apply.
A.Lns.exe
B.Lads.exe
C.FileAlyzer
D.ADSCheker
300-165 vce Answer: A,B,C
16.In order to idnetify a unique record within a database what would you use?
A.A foreign key
B.A primary key
C.A view
D.A unique key
Answer: B
17.Why is it important to the security of a network to create a complex password for the SA account on a
MSSQL server installation?
A.The SA account is a pseudo-account and does not have any privileges.
B.The SA account can add/delete or change Domain User accounts.
C.The SA account can have privileges of the local adminstrators group on the host OS.
D.The SA account is the most powerful account on the domain controller.
300-165 exam Answer: C
18.Bryce, who is a great security professional with a perfect track record,has just been called into his
supervisor’s office.His supervisor has the sad task of letting him know that hes the next position being cut
in their downsizing effort.Bryce has been known to be a mellow type of person but the version of being
unemployed after working for 25 years at the same company is just a bit too much for him.He cannot
understand why newer employees with only a few years of experience have not been fired before him and
why he is the one that must leave.Bryce tells himself that is employer is going to pay dearly for this and
hes planning to use his skills to cause disruption within the company infrastructure.Which of the following
term would best describe the reaction of Bryce?
A.Cracker
B.Disgruntied Employee
C.Ethical Hacker
D.Revenge Master
300-165 dumps Answer: B
19.Using Netcat what would be the syntax to setup a listening back door from a compromised Windows
Server that will spawn a shell when connecting to the remote server on port 777?
A.nc |p 777 e cmd.exe
B.nc sh p 777 e cmd.exe
C.nc |p 777 sh cmd.exe
D.nc |p 777 exec cmd.exe
Answer: A
Cisco certification 300-165 dumps validates the skills and experience of an IT professional or a student of the product or service in the interests of Cisco. Cisco Certified Network Professional Data Center https://www.pass4itsure.com/300-165.html dumps qualification is not an easy application and has been developed in a complex way.
More questions are available at: http://www.exampass.net/cisco-300-170-dumps.html