You may get questions from different web sites or books, but logic is the key. Cisco 300-207 exam sample questions will help you not only pass in the first try, but also save your valuable time. FLYDUMPS Cisco https://www.leads4pass.com/300-207.html practice exam is the most thorough, accurate, and up-to-date practice exams you will find on the market today. With Cisco 300-207 Questions and Answers, FLYDUMPS Cisco 300-207 study guide gives you the confidence in knowing that you will pass this difficult exam on the first try. With Cisco 300-207 exam sample questions, you can test your knowledge and readiness for exam, assess your performance in a given time, gets scores and highlighted weaknesses with suggestions to improve the weak areas.
QUESTION 26
What is the CLI command to create a new Message Filter in a Cisco Email Security Appliance?
A. filterconfig
B. filters new
C. messagefilters
D. policyconfig– inbound or outbound– filters Correct Answer: B
Explanation Explanation/Reference:
QUESTION 27
A Cisco Email Security Appliance uses which message filter to drop all executable attachments entering and leaving the Cisco Email Security Appliance?
A. drop-exE. if (attachment-filename == “\\.exe$”) OR (attachment-filetype == “exe”) { drop(); }
B. drop-exE. if (recv-listener == “InboundMail” ) AND ( (attachment-filename == “\\.exe$”) OR (attachment-filetype == “exe”)) { drop(); }
C. drop-exe! if (attachment-filename == “\\.exe$”) OR (attachment-filetype == “exe”) { drop(); }
D. drop-exe! if (recv-listener == “InboundMail” ) AND ( (attachment-filename == “\\.exe$”) OR (attachment-filetype == “exe”)) { drop(); }
Correct Answer: A Explanation
Explanation/Reference: QUESTION 28
What can Cisco Prime Security Manager (PRSM) be used to achieve?
A. Configure and Monitor Cisco CX Application Visibility and Control, web filtering, access and decryption policies
B. Configure Cisco ASA connection limits
C. Configure TCP state bypass in Cisco ASA and IOS
D. Configure Cisco IPS signature and monitor signature alerts
E. Cisco Cloud Security on Cisco ASA
Correct Answer: A Explanation
Explanation/Reference:
QUESTION 29
Which is the default IP address and admin port setting for https in the Cisco Web Security Appliance?
A. http://192.168.42.42:8080
B. http://192.168.42.42:80
C. https://192.168.42.42:443
D. https://192.168.42.42:8443
Correct Answer: D Explanation
Explanation/Reference:
QUESTION 30
Which port is used for CLI Secure shell access?
A. Port 23
B. Port 25
C. Port 22
D. Port 443
Correct Answer: C Explanation
Explanation/Reference:
QUESTION 31
Which Cisco technology prevents targeted malware attacks, provides data loss prevention and spam protection, and encrypts email?
A. SBA
B. secure mobile access
C. IPv6 DMZ web service
D. ESA
Correct Answer: D Explanation
Explanation/Reference: QUESTION 32
Which Cisco technology combats viruses and malware with virus outbreak filters that are downloaded from Cisco SenderBase?
A. ASA
B. WSA
C. Secure mobile access
D. IronPort ESA
E. SBA
Correct Answer: D Explanation
Explanation/Reference:
QUESTION 33
Which Cisco WSA is intended for deployment in organizations of up to 1500 users?
A. WSA S370
B. WSA S670
C. WSA S370-2RU
D. WSA S170
Correct Answer: D Explanation
Explanation/Reference:
QUESTION 34
Which Cisco WSA is intended for deployment in organizations of more than 6000 users?
A. WSA S370
B. WSA S670
C. WSA S370-2RU
D. WSA S170
Correct Answer: B Explanation
Explanation/Reference:
QUESTION 35
Which command verifies that the correct CWS license key information was entered on the Cisco ASA?
A. sh run scansafe server
B. sh run scansafe
C. sh run server
D. sh run server scansafe
Correct Answer: B Explanation
Explanation/Reference: QUESTION 36
Which five system management protocols are supported by the Cisco Intrusion Prevention System? (Choose five.)
A. SNMPv2c
B. SNMPv1
C. SNMPv2
D. SNMPv3
E. Syslog
F. SDEE
G. SMTP
Correct Answer: ABCFG Explanation
Explanation/Reference:
QUESTION 37
Which four statements are correct regarding management access to a Cisco Intrusion Prevention System? (Choose four.)
A. The Telnet protocol is enabled by default
B. The Telnet protocol is disabled by default
C. HTTP is enabled by default
D. HTTP is disabled by default
E. SSH is enabled by default
F. SSH is disabled by default
G. HTTPS is enabled by default
H. HTTPS is disabled by default
Correct Answer: BDEG Explanation
Explanation/Reference:
QUESTION 38
Which two GUI options display users’ activity in Cisco Web Security Appliance? (Choose two.)
A. Web Security Manager Identity Identity Name
B. Security Services Reporting
C. Reporting Users
D. Reporting Reports by User Location
Correct Answer: CD Explanation
Explanation/Reference:
QUESTION 39
The security team needs to limit the number of e-mails they receive from the Intellishield Alert Service. Which three parameters can they adjust to restrict alerts to specific product sets? (Choose three.)
A. Vendor
B. Chassis/Module
C. Device ID
D. Service Contract
E. Version/Release
F. Service Pack/Platform
Correct Answer: AEF Explanation
Explanation/Reference:
QUESTION 40
What three alert notification options are available in Cisco IntelliShield Alert Manager? (Choose three.)
A. Alert Summary as Text
B. Complete Alert as an HTML Attachment
C. Complete Alert as HTML
D. Complete Alert as RSS
E. Alert Summary as Plain Text
F. Alert Summary as MMS
Correct Answer: ABC Explanation
Explanation/Reference:
QUESTION 41
With Cisco IDM, which rate limit option specifies the maximum bandwidth for rate-limited traffic?
A. protocol
B. rate
C. bandwidth
D. limit
Correct Answer: B Explanation
Explanation/Reference:
QUESTION 42
Which two benefits are provided by the dynamic dashboard in Cisco ASDM Version 5.2? (Choose two.)
A. It configures system polices for NAC devices.
B. It forwards traffic to destination devices.
C. It provides statistics for device health.
D. It replaces syslog, RADIUS, and TACACS+ servers.
E. It automatically detects Cisco security appliances to configure.
Correct Answer: CE Explanation
Explanation/Reference:
QUESTION 43
Which Cisco monitoring solution displays information and important statistics for the security devices in a network?
A. Cisco Prime LAN Management
B. Cisco ASDM Version 5.2
C. Cisco Threat Defense Solution
D. Syslog Server
E. TACACS+
Correct Answer: B Explanation
Explanation/Reference:
QUESTION 44
Which three search parameters are supported by the Email Security Monitor? (Choose three.)
A. Destination domain
B. Network owner
C. MAC address
D. Policy requirements
E. Internal sender IP address
F. Originating domain
Correct Answer: ABE Explanation
Explanation/Reference:
QUESTION 45
Which Cisco Security IntelliShield Alert Manager Service component mitigates new botnet, phishing, and web-based threats?
A. the IntelliShield Threat Outbreak Alert
B. IntelliShield Alert Manager vulnerability alerts
C. the IntelliShield Alert Manager historical database
D. the IntelliShield Alert Manager web portal
E. the IntelliShield Alert Manager back-end intelligence engine
Correct Answer: A Explanation
Explanation/Reference:
QUESTION 46
A network engineer can assign IPS event action overrides to virtual sensors and configure which three modes? (Choose three.)
A. Anomaly detection operational mode
B. Inline TCP session tracking mode
C. Normalizer mode
D. Load-balancing mode
E. Inline and Promiscuous mixed mode
F. Fail-open and fail-close mode
Correct Answer: ABC Explanation
Explanation/Reference:
QUESTION 47
What is the correct deployment for an IPS appliance in a network where traffic identified as threat traffic should be blocked and all traffic is blocked if the IPS fails?
A. Inline; fail open
B. Inline; fail closed
C. Promiscuous; fail open
D. Promiscuous; fail closed
Correct Answer: B Explanation
Explanation/Reference:
QUESTION 48
Which two practices are recommended for implementing NIPS at enterprise Internet edges? (Choose two.)
A. Integrate sensors primarily on the more trusted side of the firewall (inside or DMZ interfaces).
B. Integrate sensors primarily on the less trusted side of the firewall (outside interfaces).
C. Implement redundant IPS and make data paths symmetrical.
D. Implement redundant IPS and make data paths asymmetrical.
E. Use NIPS only for small implementations.
Correct Answer: AC Explanation
Explanation/Reference:
QUESTION 49
Which set of commands changes the FTP client timeout when the sensor is communicating with an FTP server?
A. sensor# configure terminal sensor(config)# service sensor sensor(config-hos)# network-settings sensor(config-hos-net)# ftp-timeout 500
B. sensor# configure terminal sensor(config)# service host sensor(config-hos)# network-settings parameter ftp sensor(config-hos-net)# ftp-timeout 500
C. sensor# configure terminal sensor(config)# service host sensor(config-hos)# network-settings sensor(config-hos-net)# ftp-timeout 500
D. sensor# configure terminal sensor(config)# service network sensor(config-hos)# network-settings sensor(config-hos-net)# ftp-timeout 500
Correct Answer: C Explanation Explanation/Reference:
QUESTION 50
What are two benefits of using SPAN with promiscuous mode deployment? (Choose two.)
A. SPAN does not introduce latency to network traffic.
B. SPAN can perform granular scanning on captures of per-IP-address or per-port monitoring.
C. Promiscuous Mode can silently block traffic flows on the IDS.
D. SPAN can analyze network traffic from multiple points. Correct Answer: AD
Explanation Explanation/Reference:
QUESTION 51
What are the initial actions that can be performed on an incoming SMTP session by the workqueue of a Cisco Email Security Appliance?
A. Accept, Reject, Relay, TCPRefuse
B. LDAP Verification, Envelope Sender Verification, Bounce Verification, Alias Table Verification
C. Recipient Access Table Verification, Host DNS Verification, Masquerading, Spam Payload Check
D. SMTP Authentication, SBRS Verification, Sendergroup matching, DNS host verification Correct Answer: A
Explanation Explanation/Reference:
QUESTION 52
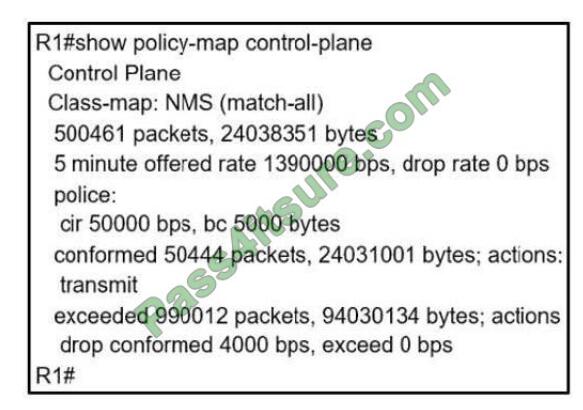
Refer to the exhibit.
What CLI command generated the output?
A. smtproutes
B. tophosts
Flydumps.com Cisco https://www.leads4pass.com/300-207.html practice tests hold the key importance and provide a considerable gain for your knowledge base. You can rely on our products with unwavering confidence; Get the profound knowledge and become a pro with Flydumps.com assistance.